It almost sounds like I’m going to give you some inner-secrete to penetrate gmail and get the keys to everything. Well, I’m not. Seriously, there’s a major flaw in gmail (namely DKIM) and I found it due to a marketing email that I get roughly 10 times a day.
The magic email
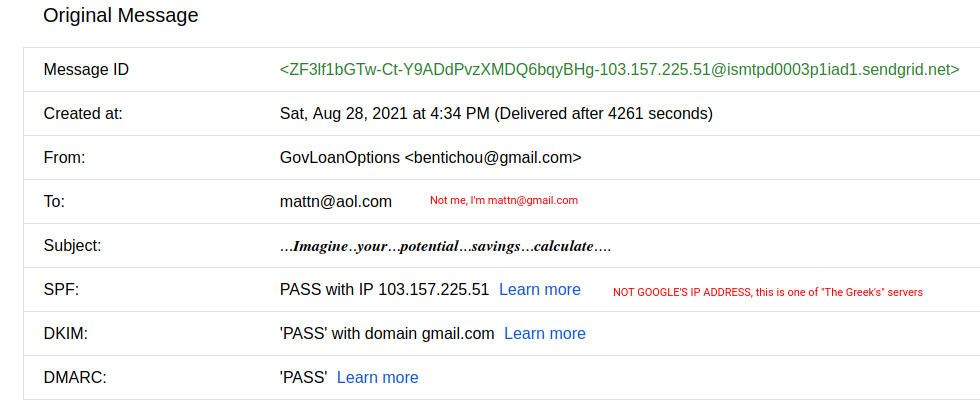
This gmail hack comes from the SAME person who emails me consistently 10x/day. It’s important to note that he’s mailing my personal gmail address, not G-Suite. I looked at the mail headers and I saw www.takataka.gr (realshop.gr) as one of the hops. Me being me, I named these mailers “The Greeks”. Chances are that they aren’t Greek, it’s just the hacked gmail headers that I was looking at.
But what makes this email so neat is that they are sending to mattn@gmail.com**
Quick sidenote here. This is NOT my real gmail, but I’m just using this as an email. I DID use my real email on this website: mattn@gmail.com and I think I attracted every website developer in India. Seriously, thanks but no thanks my Indian dudes, I don’t want web/app/android/ios development OR SEO. But I appreciate the 20 emails/day asking me if I want it. Somehow, this isn’t spam…it’s cold B2B outreach! Love these stupid can-spam laws, what a joke.
At any rate, going back to “The Greek” gmail hack. The email SHOULD be going to mattn@gmail.com but the TO is mattn@aol.com and the CC is also mattn@aol.com. I mean, yeah, it’s spam alright. Trying to sell me on the most mailed out affiliate networks available….however, it’s INBOXING! Did I mention that there’s 0 text in the email? Did I mention that it’s just two or three spammy images? I didn’t? Well…now I did.
So, naturally when garbage is inboxing on gmail, I take notice. I take massive notice! How did they hack gmail!? I sat down for two weeks to figure it out. Maybe it would take you less time, maybe you’re smarter. Anyways, it took me two weeks to figure it out. I’m going to take you down the rabbit hole that I went down.
Hack gmail online
Yeah, that’s just an SEO keyword headline…kinda. I registered a new gmail account and I started playing around with it. Namely, I wanted to see if I could do what they were doing with the account. Suffice to say, I had no luck. I could send emails through gmail’s SMTP with the gmail account, which didn’t help me. The Greeks were signing as gmail, but the IP associated with the sending was their own. WHAT?
Even beyond that, the most insane part is the signing. So, let me explain how gmail signs emails.
The Greeks are specifically signing:
message-id, date and from
Strange! Google ALWAYS signs the emails like this:
mime-version, references, in-reply-to, from, date, message-id, subject, to
This is where I was stumped, as nothing else made any sense to me. HOW could google allow this. Did the Greeks steal Big G’s private key? I highly doubt it. Did they pay off somebody to give it to them? This isn’t Yahoo where you can payoff a corrupt postmaster (this is seriously a thing, incoming future blog post!). What was going on?
This drove me insane. I tried making my own google.com keys so that I could sign my own emails by hacking my nameserver to tell me that I was Google. This would pass, but the problem up-stream is that it eventually doesn’t sign. You see, the header looks like this:
dkim=pass header.i=@gmail.com header.s=20161025 header.b=Niq+5OEI;
spf=pass (google.com: domain of from@gmail.com designates 209.85.220.41 as permitted sender) smtp.mailfrom=from@gmail.com;
dmarc=pass (p=NONE sp=QUARANTINE dis=NONE) header.from=gmail.com
Return-Path: <from@gmail.com>
Received: from mail-sor-f41.google.com (mail-sor-f41.google.com. [209.85.220.41])
by mx.google.com with SMTPS id c7sor164588lft.6.2021.07.12.20.11.30
for <to@gmail.com>
(Google Transport Security);
Mon, 12 Jul 2021 20:11:30 -0700 (PDT)
Received-SPF: pass (google.com: domain of from@gmail.com designates 209.85.220.41 as permitted sender) client-ip=209.85.220.41;
Authentication-Results: mx.google.com;
dkim=pass header.i=@gmail.com header.s=20161025 header.b=Niq+5OEI;
spf=pass (google.com: domain of from@gmail.com designates 209.85.220.41 as permitted sender) smtp.mailfrom=from@gmail.com;
dmarc=pass (p=NONE sp=QUARANTINE dis=NONE) header.from=gmail.com
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=20161025;
h=mime-version:references:in-reply-to:from:date:message-id:subject:to;
bh=tCGqwgGIK74J6PZjfWg9WcuvRF9uOKRqedDBZOd3wWs=;
b=Niq+5OEIXePJ5pKfUCSgPEjlTzfCcsFZ/Eos256ok+06eH2vH/xykWS31XfYglVJ16
XpWQGn6d0ryopqZzqqt6FqgtoUiBxC6YYHoVHI73R6HdXbfJ6+6Gc0iaYREQP1xYxJDl
Nv/AAMD7+furQ1uLWyvtP2TRBcgBGeo7dR3hjNyZn1oq0tRE+oF4aN9TfiIVyLgDxr3z
SyhtY1uvEZi8no6tQSE3GKOyTUdSxf2/55Y/KdYl0Pg1dinnjsAOwo+Ggy4yQsRLIwB3
eZ5QxRuYTxK6LGdl4cmSk+eNDfksQqHnAcSfwT9gge18ayzq3goAGIMqr/F77dkHO4YD
nHyA==
So, we know that Google is immediately signing these emails and giving back a result. The wacky part is that you CAN change parts of the email and still pass DKIM. Weird right?
So, going back to the Greeks. They are doing some wacky stuff.
- There are three parts of content in every email they sent.
- Short nonsense content
- The actual offer
- Long nonsense content
-
All of the content is in Hexa encoding, or as you and the rest of the world know it as base64.
-
Content is hosted on google drives, AWS…basically high reputation domains that aren’t every going to get blacklisted.
-
They aren’t doing any sort of tracking…weird right? It’s just a blanket spam blast. I’ve been getting the same emails now for 7 or 8 years and never clicked a link on any of them, hadn’t even opened one until recently.
-
They blast me about 10 times a day. They inbox less than I had originally thought, at around 40-50%. Some days they only get 1 to my inbox.
-
They are leveraging Google’s reputation to sign the emails, while mailing off of ‘meh’ IP ranges. ALWAYS European servers.
-
They never mail from the same IPs. At the rate they are going, they’ve probably mailed most of ipv4 themselves (obvious joke is obvious).
-
They never mail from the same domains. Always using .com or .net, they aren’t skimping out on cheap TLDS.
-
They mail the EXACT emails that affiliate companies like W4 want you to mail, so they are 100% compliant. Which is almost mind-blowing, because that stuff never ever inboxes because it’s been completely mailed out.
………so yeah, it’s an expensive operation. With lots of servers, lots of emails going out daily and lots of domains. Very churn and burn. Lots of work. But…piles of money. And that’s why you’re still reading. And you should NOT do this. They are doing it, but they shouldn’t be. I’m going on record as saying you should NOT forge headers and you should NOT hack gmail online. Don’t do it! Did you hear me Google Lawyers…I’m telling people NOT to do this. But seriously, fix yer stuff.
So, truth be told. I never got their method down 100%. I’ve yet to figure out how to completely change the headers that gmail is signing.
It’s worth noting that I tried this:
-
Setup DNS to actually claim it was google.com & gmail.com
-
Setup postfix on that server to have @gmail.com emails signing using this domain.
-
Setup postfix on another server to receive the email and then to work with the script to actually send the email out with the forged headers.
I setup my “hacked” DNS and a server that claims to be gmail.com, generated my own keys for DKIM signing, making it match gmail’s exact TXT name (not value, just hame), had @gmail.com hosted on my own server (because DNS tells it that I am @gmail.com at least for my hacked DNS).
This did not work, obviously. When the DNS call was made to match the header with the private key, it failed. Because I generated a different public key than gmail has. I guess I could have done some cloud computing and attempted to generate the same public key as Google, but this methodology is impossible with current computing power.
Ultimately, forging the headers to hack gmail online with THIS setup failed. Sorry, had to say it again. But yeah, I didn’t figure it out to that capacity. However, I did figure it out. And I’m going to share the process with you.
How to hack gmail online
Here’s what you need to get started.
-
Postfix setup and signing emails properly. I used mail-in-a-box on a super-duper cheap VPS. You might get lucky and get an IP that hasn’t been mailed out to death. Check the IP in mxtoolbox before configuring the server. If it’s blacklisted, don’t even bother with the setup, you’ll NEVER inbox. And to be fair, you might not inbox if the IP is bad enough. Anyways. Setup Postfix. It won’t work with PMTA, no idea why. I think PMTA hates the injection process? I’m sure it COULD work, but postfix was a WAY easier setup, so that’s what I did. You’ll need to setup relaying, it’s super simple and covered in the video.
-
Create a new gmail that isn’t tied to you.
-
Send an email FROM your new gmail account TO an email on your postfix server.
-
Copy the email exactly as it is starting (and including) the line “X-Original-To:”. Do NOT copy anything before that. Save this in a file called email.eml.
-
You are not going to inject this email into your postfix server, however, you are going to change the return-path to whatever@YOUR_POSTFIX_SERVER.COM and change the mail_to (NOT in the email.eml file) to whoever you want to send the email to.
-
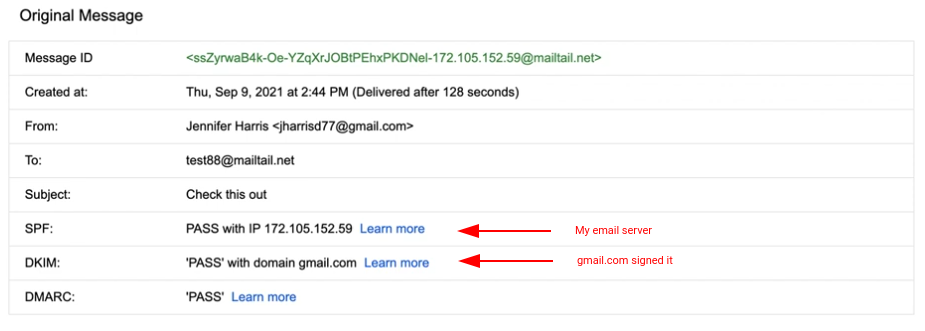
Check your mail, it should look something like this:
That’s the overall process. Now, let’s get into the code on how to hack gmail online. Oh, there’s that stupid phrase again. haha.
Watch the video at the top of this post, it shows you exactly what to do. This shows the exact process, including how to setup the code, what goes where and how it should look. Passwords changed to protect myself. Don’t hack me bro!
gmailspoofer code
Clone this repository gmailspoofer
The code is available and free on github.
Again, this is a HUGE problem with DKIM. I know I didn’t do it exactly the same, but hey…This should get you going in the right direction. Now you can have INSANTLY warm domain reputation, I hear gmail.com is pretty toasty (regarding domain reputation).
Disclaimer: Don’t hack gmail online. Don’t do this. Don’t try to monetize this. I am only showing you a flaw with DKIM. Don’t be evil!
I am Matt matt@emailhacking.net. You can reach me at (412) 960-2966.